2
2/5 Phishing Attacks
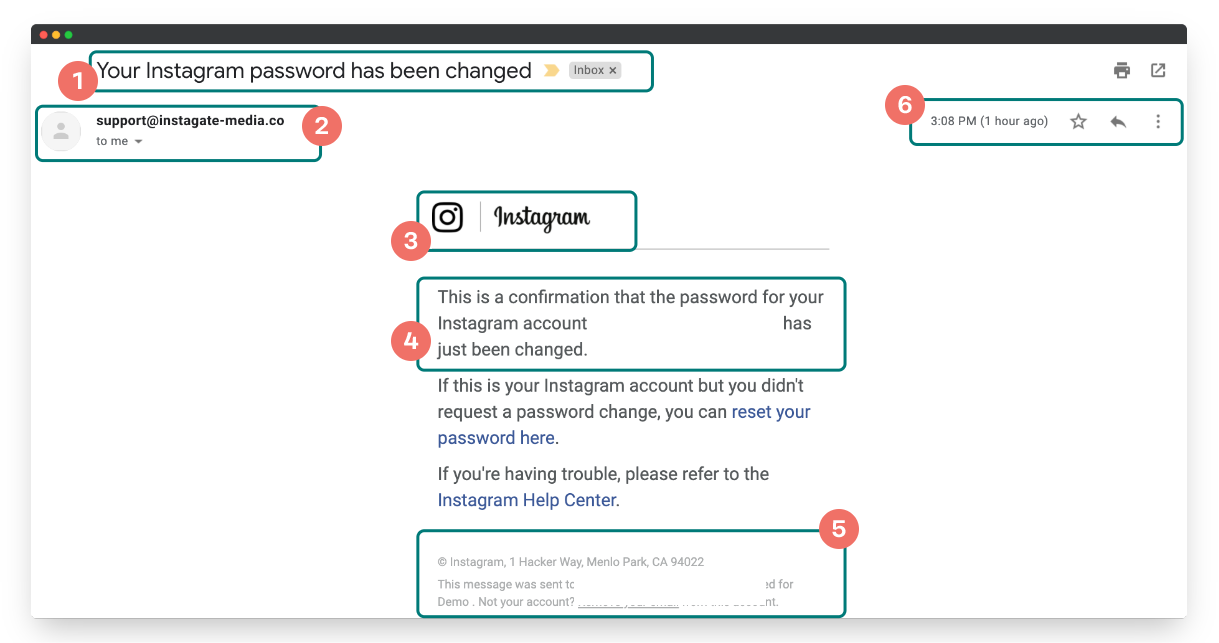
Email attacks are growing in popularity. Take a look at a "real life" email below.
Take a look at the email below. What would you do if you received this email?
Click the link to reset your password.
This email is actually a well disquised phishing attach. Clicking the link in an email like this could cause you a lot of trouble. Read more below.
Delete the email right away and move on with your life.
Good answer, deleting the email is a good way to protect yourself in this situation. Read more below about more ways to guard from phishing attacks.
Ignore the email altogether.
Ignoring the email is certainly better than clicking the link, however deleting the email altogether would protect your even more.
Delete the email, then log in to your real Instagram account to ensure that your username and password remain unchanged.
Wow! You're very diligent about privacy and data security. Keep up the good work!
Click the image to zoom in.
Phishing Attack Results
See your personalized tips below.
Data Security Learning Panel
Quick Tips
What is a phishing attack?
A phishing attack is an email engineered by hackers designed to steal personal information by getting you to do a specific task. Think about the example email above. It was designed to steal Instagram account credentials from unsuspecting users.
Key warning signs of a phishing attack:
- Any email demanding urgent action. Some of the most successful phishing attacks have disguised themselves as things like:
- An urgent email from the boss or CEO asking for an emergency wire transfer
- A subscription service that needs updated payment information within a short period of time
- An emergency request asking you to update account information
- Emails with bad grammar, misspelled words, formatting errors, or logos that don’t look right
- Unfamiliar or inconsistent email addresses, links and domain names
- Emails requesting any type of sensitive data
- Emails that are too good to be true